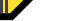World Wide
Service & Support
(800) 501-4674

|
 |
| Secure Online Order Processing |
Security Solutions |
 |
TactiCom Security Systems
TactiCom has been the choice of large and small companies worldwide, including Sterilite, Intel, Compaq, TI and the US Government. Our systems secure sensitive financial, technical, medical, government and personnel data. Our security applications include client authentication, data encryption, logging and trace systems.
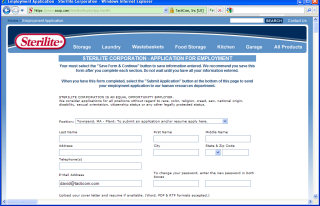
- User Authorization controls access to individual files or directories using:
- User Name & Password
- Client Certificates & Client Certificates via VPN Servers
- Two-Factor Authentication Systems (Password and Crypto Card)
- PKI digital certificates
- Domain Name (xxx.com, xxx.org, xxx.net; etc. address)
- Host Name & Client's network IP address
- SSL Encryption:
- In order to receive confidential information, such as payments over the Internet, encryption is required.
NOTE: THIS IS ONLY THE FIRST BASIC STEP IN SECURING DATA, SSL DOES NOT GUARANTEE YOUR DATA IS SECURE - JUST THE INITIAL TRANSMISSION OR COMMUNICATION OF DATA. TactiCom data security far exceeds this standard and service. Our security features are provided using the secure socket layer protocol, SSL. TactiCom uses Class 3 Extended Validation SGC SSL Certificates, with up to 256-bit encryption with a 128-bit minimum. These are considered the best and most secure SSL certificates available. Through the SSL protocol we offer:
- Server Authentication, which allows any SSL-Compatible client to verify the identity of the server using a certificate and a digital signature.
- Data encryption, which ensures the privacy of client-server communications by encrypting the data stream between the two entities (user's computer and web site) with a minimum of 128-bit encryption.
- Data integrity, which verifies that the contents of a message arrive at its destination in the same form in which it was sent.
- Database Encryption:
- TactiCom's systems can encrypt all stored sensitive data. The data, such as the contents of the tables in a database, is stored in an encrypted format. As authorized users (or applications) access their data, the data is decrypted in real time (on the fly).
If an unauthorized person was able to access the system, then the databases and breach the database security (user name / password), the information in the database would not be readable because of the TactiCom encryption.
Data encryption can be used to limit information that authorized IT personnel can access. For example, you may want database programmers, support and backup systems to be able to access the database, but not the information in the database. This solution solves the security issues with outsourcing development, hosting and data backup. Our systems are in compliance with
HIPAA, DOD & GSA supplier requirements.
- Custom Solutions:
- TactiCom develops custom security solutions for a wide range of applications. Call us at +1 (508) 393-9955 or contact us via e-mail with your requirements.
|
|

|